The growing importance of cybersecurity has made innovation in network security a top priority for governments worldwide. To encourage advancements in this field, many governments offer grants and incentives tailored to support entrepreneurs and startups. These programs not only provide financial assistance but also foster an ecosystem where groundbreaking ideas can thrive.
For cybersecurity startups, understanding these opportunities is crucial. This analysis resonates with the cybersecurity startup fundraising guide, which outlines a broad spectrum of funding strategies that set the context for government grants.
This blog serves as a comprehensive guide to exploring government grants and incentives for network-security innovation, empowering entrepreneurs to turn their ideas into impactful solutions. Whether you're just starting or scaling, these resources can be a game-changer.
Annual Funding Cybersecurity Trends
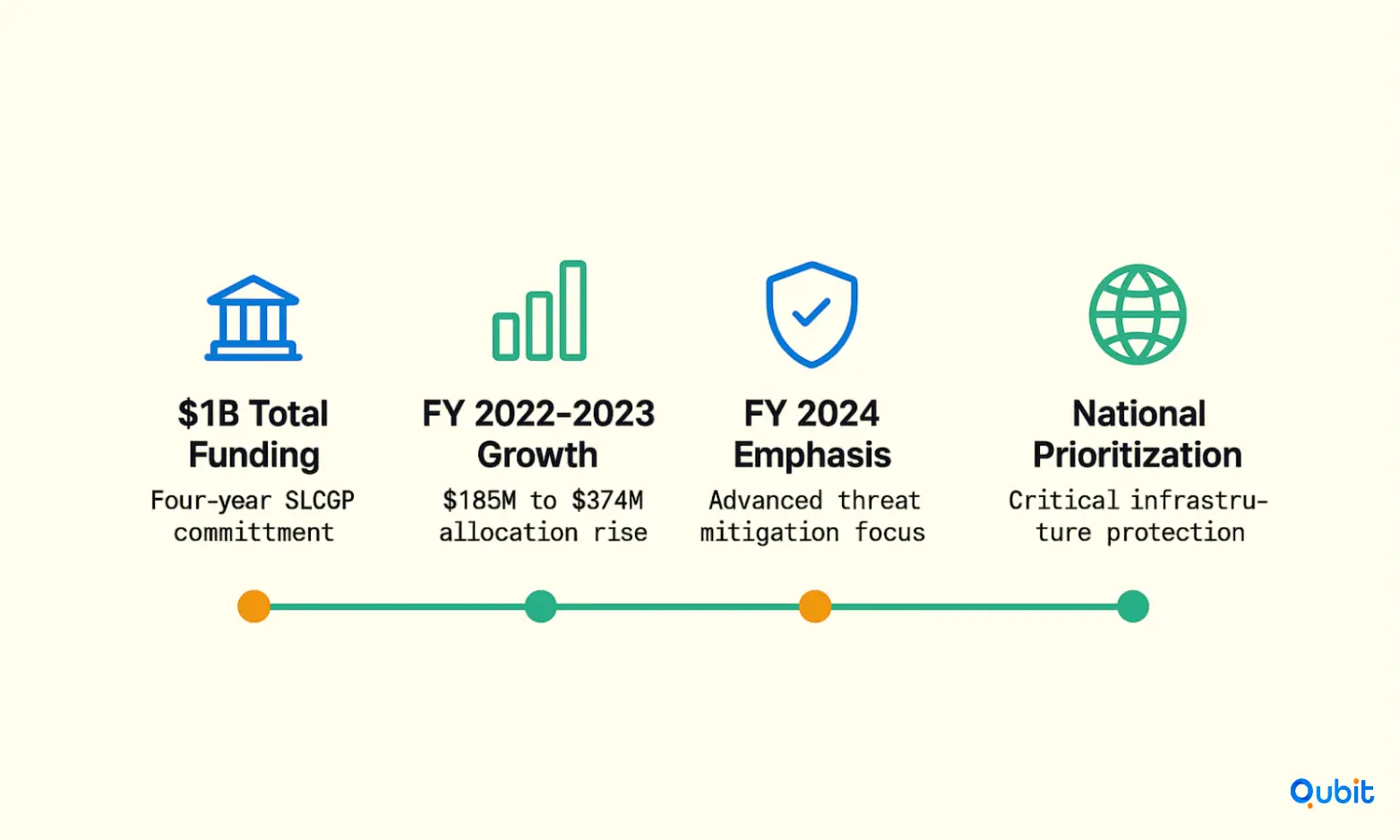
Understanding the allocation of cybersecurity grants is essential for assessing the State and Local Cybersecurity Grant Program (SLCGP). Over the past four years, the program has distributed a total of $1 billion in funding to strengthen cybersecurity infrastructure across state and local governments. This section provides a detailed look at how these funds have been allocated annually, highlighting key trends and fiscal priorities.
Breaking Down the Numbers
The SLCGP's funding allocations reveal a steady commitment to bolstering cybersecurity defenses. For Fiscal Year (FY) 2024, the Department of Homeland Security (DHS) announced a grant allocation of $279.9 million. This represents a significant portion of the program's total funding pool, emphasizing the ongoing need for robust cybersecurity measures at the state and local levels.
To put this into perspective:
- Total Funding Over Four Years: $1 billion
- FY 2024 Allocation: $279.9 million
Year-Over-Year Comparisons
Examining the year-over-year funding trends provides valuable insights into the program's evolving priorities. While earlier fiscal years laid the groundwork for foundational cybersecurity improvements, the FY 2024 allocation reflects a growing emphasis on advanced threat mitigation and resilience-building initiatives.
NOFOs and Ancillary Documents
Understanding the grant application process begins with a clear grasp of Notices of Funding Opportunity (NOFOs) and their supporting documents. NOFOs serve as the cornerstone for applicants, outlining eligibility criteria, funding priorities, and submission requirements. Alongside these, ancillary documents, such as FAQs, templates, and historical guidelines—offer additional clarity, ensuring applicants can meet all expectations.
For those seeking to align their proposals with government funding benchmarks, a review of sase zero trust cybersecurity investment metrics sheds light on performance benchmarks that intersect with criteria considered for government incentives. This connection highlights the importance of understanding both the technical and strategic aspects of grant documentation.
By thoroughly analyzing NOFOs and their supplementary materials, applicants can streamline their efforts and focus on crafting proposals that resonate with funding agencies.
Additional Supporting Documents
Streamlining the grant application process often requires more than just filling out forms. To assist applicants for FY 2023 and FY 2024, we offer an extensive library of grant supporting documents designed to simplify every step. These resources include information bulletins, project worksheets, user guides, and flow charts, all tailored to address common challenges and ensure clarity.
Tools to Simplify Your Application
Grants Repository
The Grants Repository is a centralized hub for all essential documents. From eligibility checklists to detailed project templates, this tool ensures that applicants have everything they need in one place.Applicant Video Guides
For those who prefer visual aids, the Applicant Video Guides provide step-by-step instructions on completing various sections of the application. These videos break down complex processes into manageable tasks, making it easier for both first-time and experienced applicants.
Why Supporting Documents Matter
Comprehensive supporting materials not only reduce errors but also enhance the quality of submissions. For instance, flow charts can clarify decision-making pathways, while user guides offer detailed explanations of technical requirements. These tools are designed to save time and improve the likelihood of approval.
For applicants exploring alternative funding options, insights from co-selling with hyperscalers cybersecurity funding contribute a collaborative angle, complementing the discussion on leveraging public funding opportunities.
By utilizing these resources, applicants can confidently navigate the complexities of the grant process and focus on presenting their projects effectively.
State Administrative Agency (SAA) Contacts
Finding the right point of contact for cybersecurity grants can be a daunting task. To simplify this process, we’ve compiled a comprehensive list of State Administrative Agency (SAA) contacts. These agencies are responsible for managing cybersecurity grant applications and can provide guidance tailored to your state’s requirements.
Why SAA Contacts Are Essential
State Administrative Agencies serve as the primary touchpoints for applicants seeking cybersecurity grants. They not only oversee the application process but also ensure compliance with state-specific guidelines. Whether you’re a first-time applicant or looking to renew funding, having direct access to these agencies can streamline your efforts significantly.
How to Use This Resource
Each state has its own designated SAA, complete with unique contact details and resources. Applicants should:
- Identify their state’s SAA from the list.
- Reach out via the provided contact information to clarify eligibility criteria, deadlines, and required documentation.
- Utilize any state-specific links to access additional resources or application portals.
Simplifying the Grant Application Process
For those navigating the complexities of cybersecurity grants, direct communication with your SAA can make all the difference. These agencies are equipped to answer questions, resolve issues, and provide the necessary support to ensure your application is complete and compliant.
The upcoming 2025/2026 grants for cybersecurity services present a significant opportunity for businesses and organizations to enhance their digital security frameworks. These funding programs are designed to address the growing need for robust cybersecurity measures, offering financial support to implement advanced solutions and safeguard sensitive data.
Applicants can expect streamlined application portals, detailed resource guides, and tailored funding programs to meet diverse needs. Whether you're a startup seeking initial support or an established enterprise aiming to scale your cybersecurity infrastructure, these grants provide a pathway to future-proof your operations.
An exploration of revenue based financing cloud security saas offers a comparative view of alternative funding dynamics alongside government grant options. This model complements traditional grants, enabling cybersecurity ventures to access flexible financing solutions tailored to their growth trajectory.
Stay ahead of the curve by preparing for these opportunities now. With the right resources and strategies, securing funding for your cybersecurity initiatives can become a reality.
Going Beyond SLCGP
Exploring funding opportunities beyond the State and Local Cybersecurity Grant Program (SLCGP) can open doors to innovative solutions and sustained growth. While SLCGP provides critical support, alternative funding sources offer diverse paths for cybersecurity startups to thrive.
Grants for Emerging Technologies
Government grants targeting AI-driven cybersecurity startups are gaining traction. These programs recognize the potential of artificial intelligence in enhancing security measures and are increasingly supporting projects that integrate AI into cybersecurity frameworks. For example, Cyves, a promising startup, secured a $150,000 grant from TEDCO to launch its innovative cybersecurity solution. This case highlights how startups can tap into specialized funding programs tailored to emerging technologies.
Complementary Private Funding Streams
Pairing public grants with private funding can amplify resources and accelerate growth. The perspective provided in raising capital cloud network security startups mirrors the nuances of private funding streams to pair with government grants. By combining these avenues, startups can diversify their financial base and reduce dependency on a single funding source.
Why Diversification Matters
Relying solely on SLCGP or a single government stream can limit growth. Forward-looking cybersecurity startups combine these programs with:
- Private or venture funding to extend runway and accelerate innovation
- Participation in government-backed innovation challenges for visibility and mentorship
- Co-innovation initiatives with public agencies for field-testing and market traction
Such diversification ensures resilience, supports sustained R&D, and promotes faster commercialization.
Other Grant Programs for Cybersecurity Funding
Many organizations overlook the potential of non-cybersecurity–specific grants as a means to enhance their cybersecurity infrastructure. While these grants may not be explicitly designed for cybersecurity, they can often be repurposed to address critical technology needs, including security improvements. This approach provides a creative way to secure additional resources for both operational support and long-term investments.
Identifying Grants with Flexible Applications
Certain grants, such as those aimed at education, healthcare, or community development, often include provisions for technology upgrades. For example, a grant intended to improve digital access in schools could also fund cybersecurity measures to protect student data. Similarly, healthcare grants that focus on modernizing patient record systems may allow for the integration of advanced security protocols.
Strategies for Repurposing Grants
Align Cybersecurity with Grant Objectives
To successfully repurpose a grant, it’s essential to demonstrate how cybersecurity aligns with the grant’s primary goals. For instance, if a grant is focused on improving operational efficiency, you can highlight how robust cybersecurity reduces downtime caused by breaches, ensuring smoother operations.Incorporate Cybersecurity into Broader Technology Plans
Many grants require a detailed proposal outlining how funds will be used. By embedding cybersecurity as a critical component of your overall technology strategy, you can justify its inclusion as part of the grant’s scope.Collaborate with Grant Administrators
Engaging with grant administrators early in the process can clarify whether cybersecurity expenses are permissible. Their guidance can help you tailor your application to meet both the grant’s requirements and your organization’s security needs.
Benefits of Repurposing Grants
- Increased Funding Opportunities: Expanding your search to include non-cybersecurity grants significantly broadens the pool of available resources.
- Enhanced Flexibility: These grants often allow for creative allocation of funds, enabling organizations to address multiple priorities simultaneously.
- Improved Security Posture: By integrating cybersecurity into broader initiatives, organizations can strengthen their defenses without relying solely on dedicated cybersecurity funding.
Repurposing grants not only maximizes available resources but also ensures that cybersecurity remains a priority, even when specific funding is limited.
Major Annual Cybersecurity Grant Trends
United States
The marquee State and Local Cybersecurity Grant Program (SLCGP), administered by the Department of Homeland Security (DHS) and FEMA, continues to be a cornerstone of public sector cybersecurity funding. The program aims to assist state, local, territorial, and tribal (SLT) governments in strengthening their digital infrastructure, and it reflects the increasing prioritization of cybersecurity as national critical infrastructure.
- Funding Overview:
- SLCGP totals $1 billion over four years, with over $300 million allocated just for FY 2024 and $374 million for FY 2023, following $185 million in FY 2022.
- The Tribal Cybersecurity Grant Program (TCGP) launched recently, awarding $18.2 million in its first round in 2024, further reflecting a widening scope.
- How Funds Are Used:
- Grants focus on projects to mitigate threats, improve cyber resilience, implement modern security architectures (like Zero Trust and SASE), and elevate public sector cyber maturity.
- Grantees must submit a revised Cybersecurity Plan by January 30, 2025, with detailed risk-reduction strategies.
- Projects supported range from workforce development and cyber-awareness training to deployment of next-gen firewalls and incident response capabilities.
India
- The Union Budget 2025 prioritized cybersecurity, allocating over ₹1,900 crore (approximately USD 228 million) for cyber initiatives—an 18% increase from the previous year. This underscores the nation’s commitment to fortifying vulnerability in critical infrastructure and digital services.
- The Cyber Security Grand Challenge (CSGC) 2.0 by MeitY and DSCI is focused specifically on recognizing and nurturing startups delivering cutting-edge solutions to problem statements in the sector. CSGC 2.0 will identify, directly fund, and mentor six startups per problem statement, tripling support compared to the prior edition.
Global Perspective
At the supranational level, total federal funding opportunities for cybersecurity services topped $1 billion, illustrating how governments worldwide are scaling up grants and RFPs specifically for cyber projects
Grant Programs for State/Local Governments
State and local governments face unique challenges in maintaining robust cybersecurity measures. To address these needs, a variety of specialized grant programs have been developed, targeting areas such as election security, emergency management, and critical infrastructure protection. These programs provide essential state funding grants to help governments enhance their cybersecurity frameworks and safeguard sensitive data.
Election Security Grants
Ensuring the integrity of elections is a top priority for many state and local governments. Election security grants are designed to support initiatives such as upgrading voting systems, implementing advanced cybersecurity protocols, and training personnel to detect and respond to potential threats. These grants often focus on preventing interference and ensuring transparency in the electoral process.
Emergency Management and Cybersecurity
Emergency management grant programs frequently include provisions for cybersecurity enhancements. These funds enable governments to integrate secure communication systems, protect emergency response data, and develop contingency plans for cyber incidents. By addressing vulnerabilities in emergency management systems, these grants help ensure that critical services remain operational during crises.
Infrastructure Protection Grants
Critical infrastructure, such as water systems, energy grids, and transportation networks, is increasingly targeted by cyber threats. Infrastructure protection grants provide funding to secure these essential systems against potential attacks. This includes implementing advanced monitoring tools, conducting vulnerability assessments, and developing incident response strategies tailored to infrastructure-specific risks.
Broader Cybersecurity Initiatives
In addition to targeted programs, many grants support broader cybersecurity initiatives. These may include funding for public awareness campaigns, interagency collaboration, and the development of comprehensive cybersecurity strategies. By fostering a proactive approach, these grants empower state and local governments to stay ahead of evolving threats.
State funding grants play a pivotal role in strengthening the cybersecurity posture of state and local governments. Whether focused on election security, emergency management, or critical infrastructure, these programs provide the resources needed to address pressing challenges and protect public systems.
Conclusion
Securing government grants requires a thoughtful approach and meticulous preparation. By focusing on detailed documentation and presenting a compelling narrative, applicants can significantly enhance their chances of success. Crafting a grant application that clearly outlines objectives, impact, and alignment with funding priorities is essential.
Taking the next step is equally important. If you're ready to secure funding, explore our Fundraising Assistance service to guide you through the process. Our team is here to help you navigate the complexities of grant applications and connect you with tailored funding opportunities.
Key Takeaways
- Government grants provide significant funding opportunities, particularly through SLCGP.
- Comprehensive documentation and user guides ease the grant application process.
- Alternative funding sources can supplement traditional grant programs.
- State and local initiatives offer tailored grant opportunities for specific cybersecurity needs.
Frequently asked Questions
What government grants are available for cybersecurity startups?
Various grants, including the State and Local Cybersecurity Grant Program (SLCGP) and state-specific initiatives, provide targeted funding opportunities for cybersecurity innovation. These programs are designed to help startups address early-stage financing gaps and scale their solutions effectively.






