By early 2024, global IoT market revenue was projected to reach $947.5 billion. This figure underlines how digital transformation and proliferation of IoT devices are creating enormous commercial opportunities. For both startups and investors, such market scale ensures continued funding interest and competitive pressure.
2025 is marked by rapid digitalization, a surge in cyber threats, and a funding environment that is both competitive and full of opportunity. As operational technology (OT) and Internet of Things (IoT) systems become increasingly interconnected, and essential to critical infrastructure, the demand for robust security solutions has never been greater. For founders and investors alike, understanding the funding dynamics, valuation trends, and strategic priorities shaping this market is crucial for success.
This article provides a comprehensive view of the funding landscape for IoT/OT security startups, drawing on the latest market data, investor sentiment, and startup strategies.
Let's jump right in!
Market Overview: Growth, Drivers, and Challenges
IoT/OT security startups face a competitive but opportunity-rich funding environment shaped by rapid digitization, investor demand, and new compliance drivers.
OT Security Market Growth and IoT Acceleration
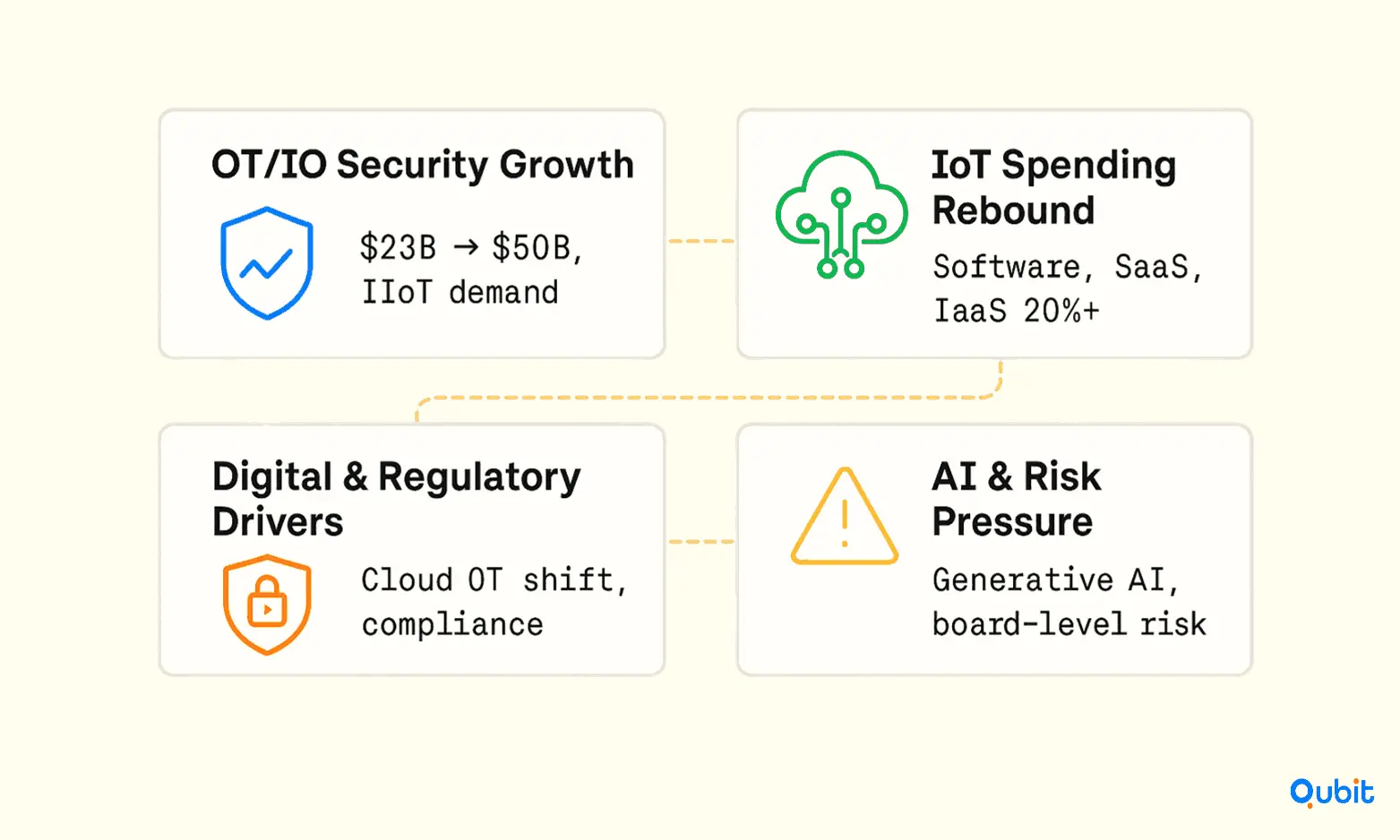
Growth in OT security is accelerating. The OT security market is projected to grow from $23.47 billion in 2025 to $50.29 billion by 2030, which works out to a 16.5% CAGR. That pace signals a fast-moving market where buyers will keep upgrading defenses, and vendors will face tighter competition as new tools and managed services crowd in.
A big driver is the expanding footprint of connected industrial systems. As more IIoT devices, sensors, and connected equipment get deployed across manufacturing, energy, and utilities, efficiency goes up, but so does the attack surface. Forecasts suggest connected IoT devices could reach roughly 39 billion by 2030. That scale makes security less like an “IT nice-to-have” and more like basic operational insurance for critical infrastructure.
Spending patterns also support this shift. Enterprise IoT spending grew 10% in 2024, its slowest pace in over a decade, but indicators point to a rebound in 2025. Even during the slowdown, software stayed strong. IoT Analytics reports that IaaS supporting IoT deployments and SaaS supporting IoT deployments still grew 22% and 21% year over year. That resilience is a strong signal that software-led OT security and managed services will keep attracting budget and investment, even when hardware cycles cool off.
Key Funding Drivers
- Digital Transformation: The shift to digitized, cloud-connected OT environments increases both efficiency and vulnerability, driving demand for advanced security frameworks.
- Regulatory Pressure: Governments worldwide are tightening cybersecurity regulations for critical infrastructure, making compliance a key motivator for security investment.
- AI and Analytics: The integration of AI for threat detection and response is now a must-have, with generative AI enabling real-time anomaly detection and adaptive defenses.
- Physical and Financial Risk: High-profile incidents (e.g., ransomware attacks on power grids) have highlighted the real-world impact of OT security failures, making investment in this space a board-level priority.
Market Challenges
- Securing legacy systems
- Talent shortages
- Procurement costs
- Integration complexity
Startups targeting highly regulated healthcare sectors may face longer sales cycles and require additional certifications beyond typical industrial compliance. Institut Mines-Télécom incubators now support over 80 new projects yearly, each with a five-year survival rate above 80%. These ventures raised €100 million, creating 5,000 sector jobs. Such metrics reinforce viability and growth of OT/IoT startup activity.
Funding Trends: Where the Money Is Flowing
Cybersecurity remains one of the most active and well-funded sectors in tech, with IoT/OT security occupying a unique and increasingly prominent niche. While cloud security, data security, and IAM command the highest valuation multiples, OT/IoT security is now seen as an undervalued sector with strong upside for both investors and acquirers.
In 2025, almost 1% of startups worldwide operate in Cybersecurity. This sizable presence demonstrates persistent investor demand and sector resilience, highlighting ongoing opportunity in OT and IoT security.
- Deal Stages: Over half of deals to connected enterprise security startups occur at the seed or Series A stage, indicating robust early-stage interest.
- Software vs. Hardware: In late 2024, 45% of the top 20 IoT startup investments were software-focused, reflecting a shift toward scalable, recurring-revenue models.
Globally in 2025, approximately 6% of startups operate in the Hardware & IoT industry. This concentration reinforces why funding continues to flow into scalable connectivity and device platforms.
- Corporate Venture Capital: Major industrial and tech players (e.g., GE, Samsung, Intel, Google) are actively investing in OT and IoT security startups, seeking both strategic advantage and financial return.
- Geographic Hotspots: North America and Asia Pacific remain the largest markets, with Asia’s growth fueled by rapid industrialization and digital adoption.
Recent success stories illustrate market traction. Cribl surpassed $200 million ARR (Annual Recurring Revenue) within only six years post-launch. This rapid growth signals strong investor confidence and robust funding outcomes in security startups.
Valuation Multiples and Benchmarking
Valuations for IoT/OT security startups are rising for SaaS (Software as a Service) and AI-driven models.
- Revenue Multiples: While public cybersecurity companies are seeing more conservative valuations in 2025, private funding and M&A (Mergers and Acquisitions) activity remain robust in high-demand segments. OT/IoT security startups are often valued at a discount to cloud/IAM peers. However, this is shifting as the market matures and high-profile breaches increase urgency.
- ARR and Funding Benchmarks: Foundational metrics such as ARR (Annual Recurring Revenue), growth rate, and customer logo quality remain central to credible valuation analysis. Early-stage startups with strong ARR growth and blue-chip customers can command premium multiples, especially if they offer SaaS or managed service models.
Fundraising across cybersecurity verticals involves diverse deal structures and investor criteria. Cybersecurity startup fundraising guide walks through the capital models, growth-stage expectations, and trend insights founders need across network security, application protection, and beyond.
Startup Strategies: What’s Winning Funding in 2025
1. AI-Driven Threat Detection and Response
Startups using AI and machine learning for real-time threat detection, anomaly analysis, and automated response are at the forefront of investor interest. Generative AI is being used to analyze vast data streams from industrial systems, predict threats, and orchestrate rapid mitigation, capabilities that appeal to both enterprise buyers and acquirers.
IoT and OT security funding starts with choosing the right capital model funding IoT/OT security startups lays out the strategies, investor benchmarks, and timing that founders in this space rely on.
2. Cloud-Native and Edge Security Solutions
With workloads moving to the cloud and edge, solutions that secure data and devices across hybrid environments are in high demand. Cloud-based OT security platforms offer scalability and easier integration, while edge security addresses latency and local processing needs.
3. Regulatory Compliance and Risk Management
Startups offering tools for compliance automation, risk assessment, and reporting are increasingly attractive, as organizations face mounting regulatory scrutiny. These solutions help enterprises navigate complex requirements and demonstrate due diligence to regulators and insurers.
4. IT/OT Convergence and Unified Security Platforms
The convergence of IT and OT systems has created demand for unified platforms that provide end-to-end visibility, network segmentation, and incident response across both domains. Startups that can bridge this gap and offer seamless integration are well-positioned to capture market share.
5. Managed Security Services for SMEs
Given the high cost and complexity of OT security, managed service providers (MSPs) targeting small and medium enterprises are gaining traction. These startups offer subscription-based security monitoring, incident response, and compliance support, lowering the barrier to adoption for resource-constrained organizations.
6. Zero-Trust Architecture and Fine-Grained Access Control
Zero-trust architecture is becoming a cornerstone for IoT/OT security startups seeking to win investor confidence. This approach assumes no device, user, or system is inherently trustworthy, enforcing strict verification and least-privilege access at every layer. Startups implementing zero-trust models use dynamic credential rotation, micro-segmentation, and continuous authentication to reduce lateral movement and limit the blast radius of breaches.
Fine-grained access control further enables organizations to tailor permissions for both human and non-human identities, including autonomous agents and IoT devices.
- Design access policies that require explicit authentication for every user, device, and application interaction within the OT/IoT network.
- Implement automated credential rotation and session monitoring to minimize the risk of compromised credentials being exploited by attackers.
- Use micro-segmentation to isolate critical assets, ensuring that even if one segment is breached, the rest of the network remains protected.
7. Social Engineering Simulation and Human-Factor Defense
Beyond technical safeguards, startups are increasingly simulating social engineering attacks to uncover human-factor vulnerabilities in OT and IoT environments. This strategy involves testing employee awareness, response protocols, and susceptibility to phishing, pretexting, and other manipulative tactics. By running controlled simulations, startups can identify training gaps, improve incident response, and demonstrate a holistic approach to security that resonates with enterprise buyers.
Investors recognize that many breaches originate from human error rather than technical flaws. Startups that proactively address the human element signal operational maturity and a comprehensive risk posture. Incorporating social engineering simulation into product or service offerings can differentiate startups in crowded markets and increase their appeal to both customers and acquirers.
- Develop scenarios that mimic real-world phishing, baiting, and pretexting attacks targeting OT/IoT personnel and processes.
- Analyze simulation results to tailor employee training and strengthen organizational security culture across all operational levels.
- Integrate human-factor testing into ongoing security assessments to provide continuous improvement and measurable risk reduction.
8. Blockchain and Cryptographic Identity for Autonomous Protection
Blockchain and cryptographic identity management are emerging as powerful tools for securing IoT/OT networks. Startups leveraging these technologies create tamper-resistant records of device identities, transactions, and access events, enabling autonomous verification and privacy-preserving operations. Decentralized identity frameworks reduce reliance on central authorities, minimizing single points of failure and enhancing resilience against sophisticated attacks.
By embedding cryptographic credentials directly into devices and network layers, startups can automate trust decisions and enforce access policies without manual intervention. This approach is particularly valuable in large-scale, distributed environments where traditional identity management is complex and costly. Investors are increasingly interested in startups that use blockchain and cryptography to deliver scalable, future-proof security solutions.
- Implement decentralized identity protocols that allow devices to authenticate and authorize autonomously within the IoT/OT ecosystem.
- Leverage blockchain ledgers to create immutable audit trails for compliance, incident investigation, and regulatory reporting.
- Integrate cryptographic access controls to ensure only trusted entities can interact with critical infrastructure components.
Funding Sources: Who’s Investing and Why
1. Venture Capital and Growth Equity
Traditional venture capital remains the primary source of funding for IoT/OT security startups, with a focus on early-stage rounds (seed, Series A, Series B). Investors are seeking:
- Recurring Revenue Models: SaaS (Software as a Service) and managed services are favored for their predictability and scalability.
- Strong ARR Growth: Startups with 2x+ YoY ARR growth and expanding customer bases stand out.
- Defensible Technology: Patents, proprietary AI models, and deep integration capabilities are key differentiators.
2. Corporate Venture Capital
Corporate VCs from industrial, energy, and tech giants are highly active in the space, often co-investing with traditional VCs or leading strategic rounds. These investors bring not only capital but also access to customers, distribution channels, and industry expertise.
3. Strategic Acquisitions and M&A
Given the urgent need for OT/IoT security, established players are actively acquiring startups to fill product gaps and accelerate innovation. Startups with unique technology, proven deployments, or regulatory certifications are prime targets for M&A (Mergers and Acquisitions).
4. Government Grants and Public Funding
In regions where critical infrastructure protection is a national priority, government grants and incentives are supporting early-stage innovation. This is particularly true in Asia Pacific and Europe, where public-private partnerships are common.
Market Outlook: Trends Shaping the Next Wave
1. Digitization and Cloud Adoption
The digitization of operational environments and migration to cloud platforms are expanding the attack surface and driving demand for scalable, flexible security solutions.
2. AI and Automation
AI-powered security platforms are becoming standard, enabling proactive defense, rapid response, and continuous adaptation to evolving threats.
3. Regulatory Evolution
Stricter regulations around critical infrastructure and data privacy are raising the bar for compliance, creating both challenges and opportunities for startups.
4. Talent and Skills Gap
The shortage of skilled OT security professionals is driving demand for automation, managed services, and user-friendly platforms.
5. Edge and 5G Integration
As industrial environments adopt edge computing and 5G connectivity, startups offering security solutions tailored to these architectures are gaining investor attention.
Valuation Benchmarks and Metrics: What Investors Expect
- ARR Multiples: OT/IoT security startups are typically valued at 6–10x ARR (Annual Recurring Revenue) for high-growth SaaS models, with discounts or premiums depending on customer concentration, technology, and market timing.
- Growth Rate: 2x+ YoY ARR growth is the standard for Series A/B rounds.
- Customer Logos: Enterprise deals, especially with critical infrastructure operators, can command higher valuations.
- Retention and Expansion: High net revenue retention (>100%) and expansion revenue signal product-market fit.
- Burn Multiple: Investors favor startups with burn multiples below 3x, indicating capital efficiency.
For more on ARR benchmarks and financial modeling, see our cybersecurity startup fundraising guide.
Actionable Tips for Founders
- Focus on Software as a Service (SaaS) and Managed Services: Recurring revenue models are favored by both VCs and acquirers.
- Demonstrate Regulatory Readiness: Build compliance features and obtain relevant certifications early.
- Leverage AI and Automation: Highlight how your solution uses AI for real-time detection and response.
- Build Strategic Partnerships: Engage with corporate VCs and industry leaders for co-development and go-to-market support.
- Showcase Customer Wins: Secure and publicize deployments with marquee customers, especially in critical infrastructure sectors.
- Prepare for Due Diligence: Maintain robust financials, clear IP ownership, and a strong data room to accelerate funding and M&A (Mergers and Acquisitions) discussions.
Conclusion
As digital transformation accelerates and cyber threats grow more sophisticated, investors are doubling down on startups that can deliver scalable, AI-driven, and compliant security solutions for the world’s most critical systems. Founders who align their strategies with these market realities, and who can demonstrate strong growth, capital efficiency, and customer traction, will be best positioned to secure funding and drive the next wave of innovation.
Investors are paying attention to IoT and OT security but only the most prepared founders will secure the best deals. Avoid wasting time with the wrong investors or generic pitches.
Use our Fundraising Assistance service to get expert, industry-aware support that helps you build a compelling narrative, engage the right backers, and close rounds with confidence.
Key Takeaways
- The IoT/OT security market is rapidly growing, driven by IIoT adoption, cyber threats, and regulatory demands.
- Software and managed services dominate funding, with strong early-stage investor interest.
- Valuations vary but are rising as the market matures, especially for SaaS and AI-driven startups.
- AI and cloud adoption are key growth drivers, enabling advanced threat detection and scalable solutions.
- Challenges include legacy system security, high costs, and talent shortages.
- Industry events remain vital for networking and funding opportunities.
Frequently asked Questions
What types of investors are most active in IoT/OT security startup funding?
Venture capital funds, corporate VCs, and government programs are the top investors in IoT/OT security startups, especially for early-stage rounds.





